Barely a fortnight into the new year and already a new kind of cyber threat has raised its ugly head. In the last few weeks, a new type of phishing campaign has been noticed, which hacks into a user’s Gmail account, steals relevant information and then goes on to target the user’s Gmail contacts as new victims.
The attack was identified by cyber security experts at WordFence, the security research of blogging site WordPress.

What is phishing?
Phishing is a type of cyber attack under which emails and messages are sent from fictitious companies or people, telling users they have won a lottery or contest and requesting them to make some particular personal information public in order to physically receive the prize. Often these include bank account details or even sums of money.
The email addresses often assume a creditable personality and impersonate real institutions.
What is the new Gmail phishing attack?

The hacker behind the new phishing attacks waits for users to submit their passwords. The second a new password is entered, the hacker logs in as the user. The hacker can do this by using the new technique of phishing which employs a data uniform resource identifier (URI).
What it effectively does is create a fake Google log-in page to fool users into entering their account credentials. It does so by embedding a complete file in the browser’s location bar.
According to a report in Forbes, the hacker must be part of a team since they are very quick to act. If not a team, then there must be an automated system employed by the hacker.
Why is it more dangerous than regular phishing?
The attack has targeted Gmail accounts specifically. Going by the level of interconnectivity a Gmail account has with almost all other accounts (social media/websites/saved payment details), it is safe to say that hacking into a Gmail account is like hitting the motherload.

Once the hacker is in a particular user’s Gmail account, they rifle through the sent items and find an image attachment and use it along with a familiar ‘Subject’ line that you have already used to send phishing mails to the user’s Google contacts. Once they click on the attachment, instead of the image, a duplicitous Google account opens instead of the real account. It asks users to log in again and since the web address reads Google Accounts (https://accounts.google.com), users are fooled into believing it is a real sign-in.
Since it is using familiar content, it lends the mails more credibility and thus makes the victims more easily susceptible to clicking on the attachment.
Unlike other attacks, this kind of phishing is very hard to spot, even by those who are tech savvy and confident with electronics, since the fake Google account that opens once the account is hacked, reads exactly like a gmail account address should read in the address bar (https://accounts.google.com)
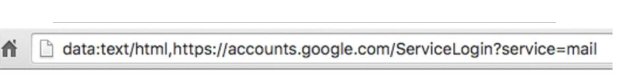
How to spot the attack ?
An easy way to ascertain out if an account is under attack is to check for the lock icon that appears on the left of the address bar when a Gmail account is open. Though this might not a foolproof solution (several phishing sites protect themselves from security these measures now)
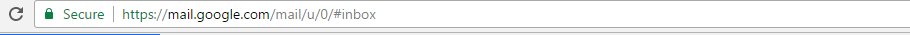
The second is to install two-factor authentication for Gmail accounts. If users do this, hacking into their Gmail password alone will not allow hackers to enter the account since authentication from another device (such as a cellphone) is necessary for login, IB Times reports.
Users need also to look out for ‘data:text/html’ as a prefix in the address bar. If this appears, the account has most definitely been hacked and is currently taking the user to a malicious site.
What to do if already under attack ?
If a user finds their account compromised, they should immediately change their password and then head to the Gmail account activity page, where users can monitor the number of sessions they are currently logged into.
Feature Image Source: Reuters/AFP

















